A really simple example
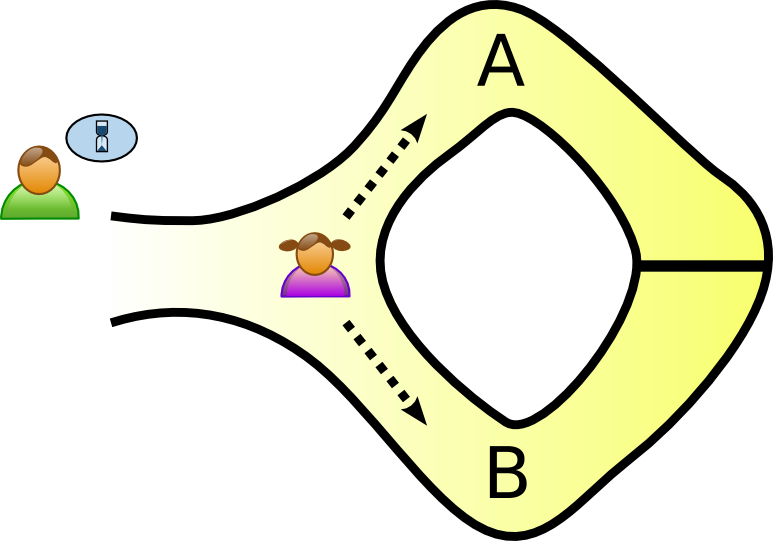
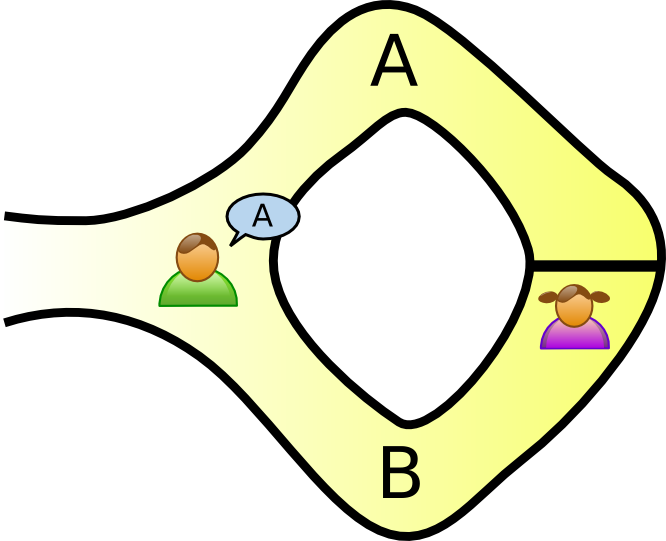
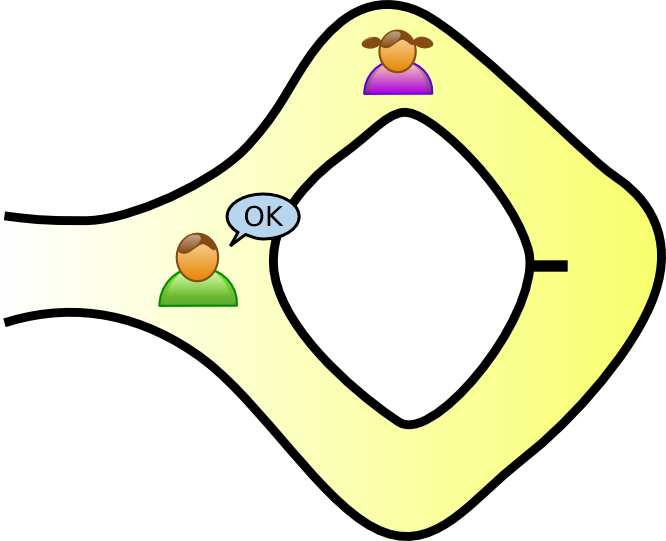
A zero-knowledge proof is an interactive method for one party to prove to another that a statement is true without revealing anything other than the veracity of the statement.
(from A Survey of Zero-Knowledge Proofs with Applications to Cryptography, A. Mohr.)
An interactive proof system is a two-party game between a verifier executing a probabilistic polynomial-time strategy and a prover which executes a computationally unbounded strategy satisfying:
An interactive proof system is zero-knowledge if the output of any strategy used by a cheating verifier could also be produced by a non-interactive computation alone.
That is, even if the verifier is trying to cheat, they learn nothing other than whether the statement is true, unless they were already able to verify the statement independently.



Graphs $G(V,E)$ and $H(V,F)$ are isomorphic iff there exists a permutation $\pi$ of the set of vertices $V$ such that \[(u,v) \in E \: \Leftrightarrow \: (\pi(u),\pi(v)) \in F\].
We have two graphs $G_0(V,E_0)$ and $G_1(V,E_1)$. V wants P to prove that they are isomorphic. Let $G_1 = \phi G_0$.
After $m$ successful iterations of these steps, V accepts P's proof.
If we can construct a zero-knowledge protocol for any NP-complete problem, it can serve as a zero-knowledge protocol for any NP problem. So, pick one!
I have a graph $G(V,E)$. Can its vertices be coloured with exactly three colours so that no edge has the same colour on both ends?
Both P and V know a graph $G(V,E)$ with $|V| = n, |E| = m$. P claims to know a 3-colouring $\phi:V \rightarrow \{1,2,3\}$ of G. Do the following $m^2$ times:
How do you play Poker over the internet without a trusted dealer? This is called mental poker.
We need to ensure the following:
The paper, A zero-knowledge Poker protocol that achieves confidentiality of the players’ strategy or How to achieve an electronic Poker face, C. Crépeau (1987), gives a zero-knowledge protocol satisfying all these requirements.
Every player $P_i$ secretly picks a shuffling of the cards $\pi_i$. The shuffled deck is $\pi = \pi_N \dots \pi_2 \pi_1$.
To pick a card, select a number $k \in \{1,\dots,52\}$ which hasn't been picked yet, and compute $\pi(k)$.
Computing $\pi(k)$ so that only the player taking the card knows its value involves lots and lots of zero-knowledge protocols.
Somebody is going to prove that they can solve my Sudoku puzzle without revealing their solution.
We'll use the protocol from Cryptographic and Physical Zero-Knowledge Proof Systems for Solutions of Sudoku Puzzles, Gradwohl, R., Naor, M., Pinkas, B., & Rothblum, G. (2007).
/
#